Alert Intelligence Policies
Alert Intelligence is a crucial process involving various policies aimed at optimizing the management and analysis of alerts. This process includes deduplication, enrichment, and aggregation of data to provide a more coherent and actionable view of alerts.
Policy Types and Category Type
Policy Types | Description |
|---|---|
Deduplicate | Removes duplicate alerts to minimize noise and redundancy. |
Enrichment | Adds context and metadata to alerts for a deeper understanding. |
Correlate | Identifies and links related alerts to reveal underlying patterns. |
Aggregate | Groups related alerts into a single, comprehensive alert for simplified management. |
Suppression | This policy is designed to suppress informational severity alerts originating from external sources. It ensures that only critical and relevant alerts are prioritized for attention, reducing unnecessary notifications. |
Category | Description |
|---|---|
Alert Handling | The process of managing and responding to alerts includes categorizing, prioritizing, and taking appropriate actions to address or resolve the issues indicated by the alerts. This involves deduplication, enrichment, correlation, and aggregation of alerts to streamline and enhance the efficiency of incident response and system monitoring. |
Deduplication: This step involves identifying and removing duplicate alerts to ensure that unique alerts are processed and analyzed. This reduces noise and allows for more efficient handling of alert data.
name: "Bugbash_Dedup_Policy" description: "Deduplicate External alerts." criteria: "event_provider: Others AND -status: Closed AND entity_id: 110667" precedence: 1 category: "alert_handling" actions: - type: "dedup" criteria: "true" query: "event_provider: Others AND -status: Closed AND entity_name: BugBash AND entity_type: BugBash" set: severity: $alert.severity summary: $alert.entity_nameEnrichment: In this phase, additional context is added to the alerts. This may include appending relevant metadata, correlating alerts with known issues, or adding information from external sources to provide a comprehensive understanding of the alert.
name: "Enrichment policy" description: "Enrich OC alerts." criteria: "event_provider: OpsCruise AND -status: Closed AND related_entities.namespace: \"robot-shop\"" precedence: 1 category: "alert_handling" actions: - type: enrich criteria: "status: Open" set: priority: "Low" description: "QA teamm modified it for testing"Aggregation: Aggregation policies group related events and alerts, identifying relationships between them. This helps in consolidating multiple alerts into a single, more meaningful alert, simplifying the alert management process.
name: "Parent Creator Rule" description: "Create new parent alert if it doesnt exist or correlate incoming alerts with existing parent alert." criteria: "event_provider: Others AND -status: Closed AND entity_type: WAN_TEST" precedence: 10 category: "alert_handling" actions: - type: "aggregate" query: "event_provider: Others" criteria: "summary: \"WAN TEST\"" parentAlert: fields: severity: "Major" matchFields: summary: "parent alert created" entity_type: "WAN_TEST" entity_id: "TEST0000006"Suppression: This policy is designed to manage alert notifications by suppressing informational severity alerts that originate from external sources. The policy ensures that non-critical alerts do not overwhelm the system, allowing users to focus on more urgent events.
name: "Suppress_Info_Alerts" description: "Suppress Info severity alerts coming from external sources" criteria: "event_provider: Others AND severity: Info" precedence: 10 category: "alert_handling" actions: - type: "suppression"
Note
We do not support special characters in policy criteria.
Note
The LuceneMemoryIndex class uses a slightly different query syntax than Solr, which affects how we evaluate "Criteria" for each phase/policy. For instance, using the criteria source: EventService AND -entity_type: (pod container) still matches pods and containers. To prevent this, you need to include OR explicitly, like -entity_type: (pod OR container).
By implementing these enrichment policies, organizations can enhance their ability to monitor and respond to critical issues, ensuring a more streamlined and effective alert management system.
Navigating to the Custom Policies:
Log in to the Virtana Global View.
Select Governance and click Alert Intelligence.
An Alert Intelligence page opens.
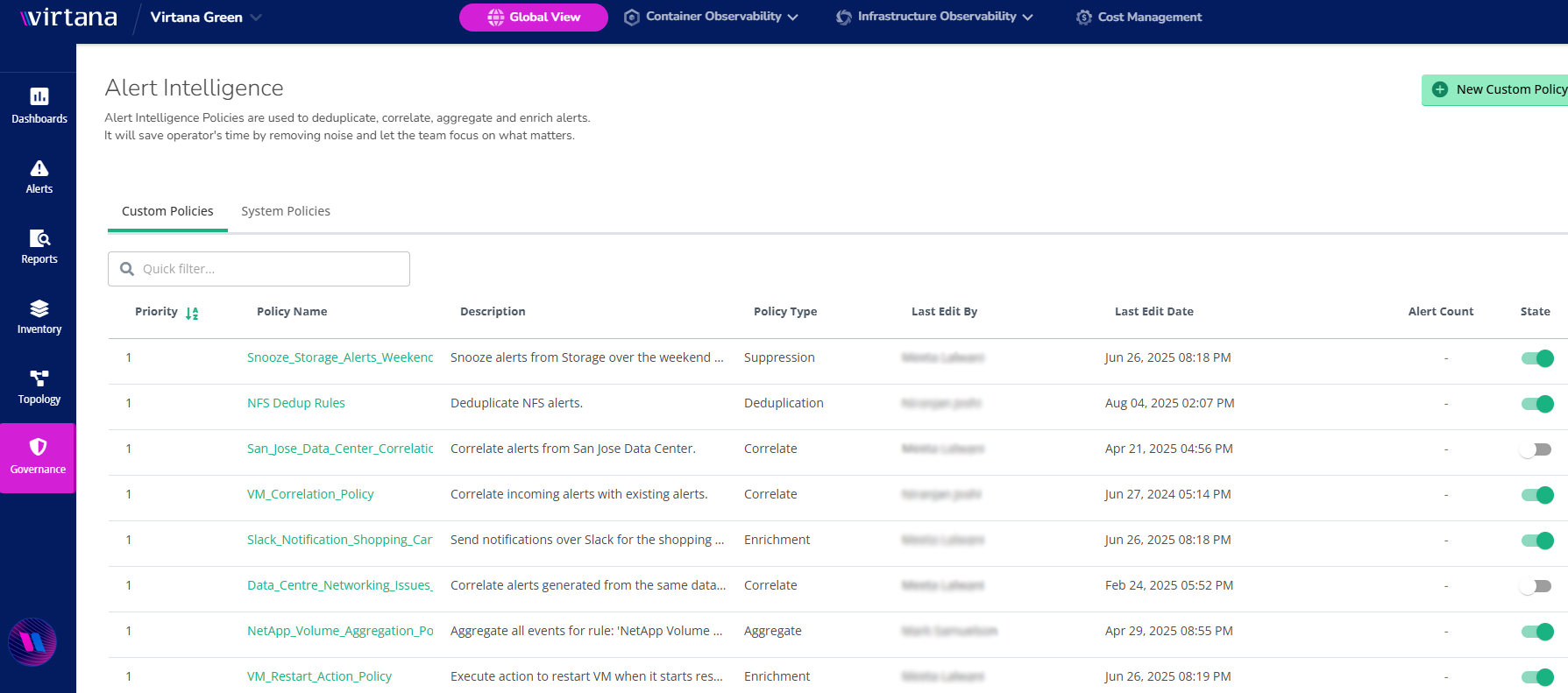
Use this table to assess the details of governance policies in one place. You can view key information, such as the policy's purpose type, the name of the user who last edited the policy, when they edited it, and the policy's current state. This centralized view allows you to efficiently monitor, manage, and adjust governance policies as needed.
Policy Name: The unique name or identifier of the governance policy.
Priority: The priority column in the governance tab indicates the relative importance or urgency of each policy. In this system, a higher number indicates a lower priority, while a lower number signifies a higher priority.
Description: A brief description explaining the purpose or focus of the policy.
Policy Type: The type or category of the policy (for example, Deduplication, Correlation, Enrichment).
Edited By: The user or team who last edited or modified the policy.
Edit Date: The date and timestamp when the policy was last edited or updated.
State: Indicates the current status of the policy (for example, enable, disable).
Note
All the properties in the alert are accessible as variables with $alert.<property_name>. These names are available under the Properties tab on the Alert details page as raw key-value pairs.
Configuring Alert Correlation Policy Using YAML
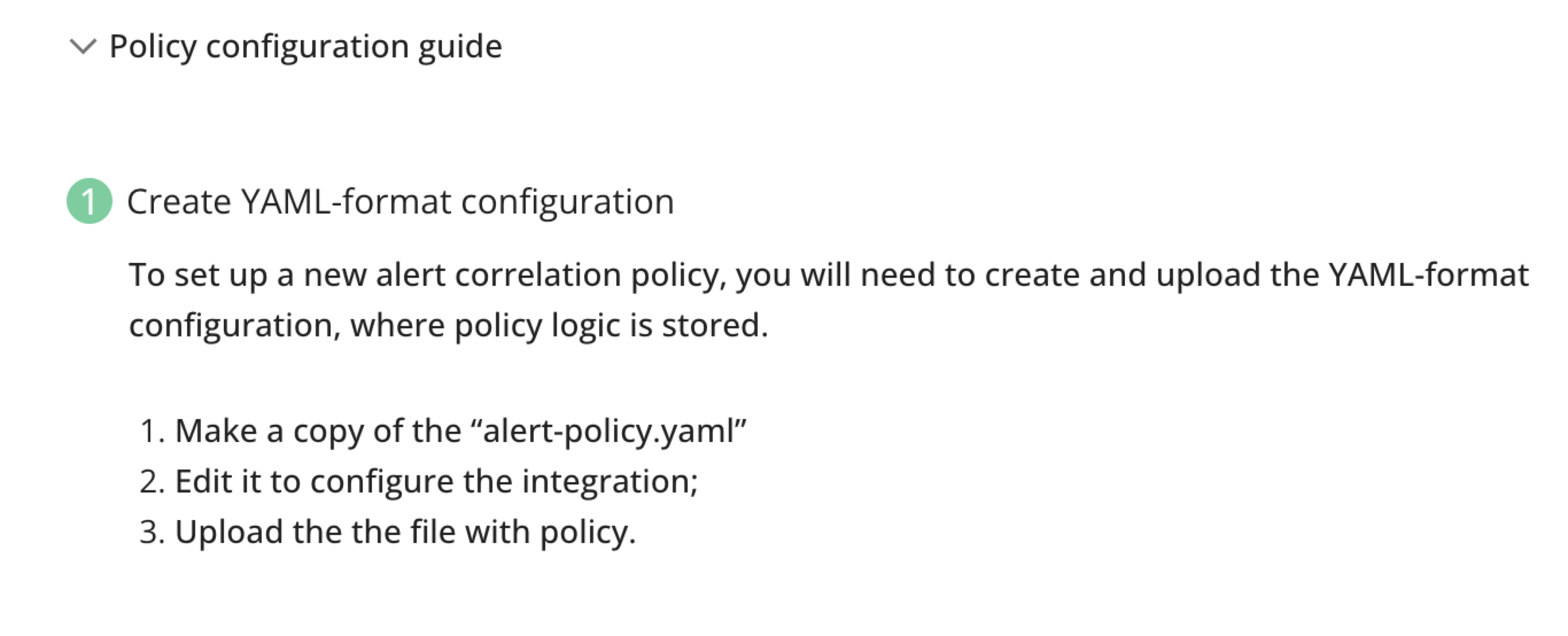
Duplicate the "alert-policy.yaml" File Make a copy of the existing "alert-policy.yaml" file.
Edit the Configuration: Modify the duplicated file to configure the integration as required for your setup.
Upload the Configured File: Use the provided upload feature to submit the edited YAML file, which contains the policy logic.
Enter the following details:
Policy Name and Description: Provide a name and a description of the policy. For client-specific policies, include relevant tenant organization names. It is not mandatory to have a Tenant ID.
policy: name: Same application description: Correlation activated because alerts generated from the same precedence: 1 category: "alert_handling"
Filter the type of alerts that occur on the selected resources. If no conditions are defined in this section, all alerts on the selected resources will match this policy.
criteria: "event_provider: OpsCruise AND -status: Closed"
Deduplicate: Removes duplicate alerts to minimize noise and redundancy.
actions: - type: "dedup" criteria: "status: Open AND priority: Highest" query: "event_provider: Others AND entity_id: $alert.entity_id AND entity_type: $alert.entity_type" set: severity: $alert.severity summary: $alert.entity_nameEnrichment: Adds context and metadata to alerts for a deeper understanding.
actions: - type: enrich criteria: "status: Open" set: priority: "Low" description: "Alert enrichment example"Correlate: Identifies and links related alerts to reveal underlying patterns.
actions: - type: "correlate" criteria: "true" elementType: "host" linkType: "parent" query: "status: Open AND entity_type: host AND entity_name: $alert.related_entities.host"
Aggregate: Groups related alerts into a single, comprehensive alert for simplified management.
actions: - type: "aggregate" query: "event_provider: Others" criteria: "summary: "WAN TEST"" parentAlert: fields: severity: "Major" matchFields: summary: "parent alert created" entity_type: "WAN_TEST" entity_id: "TEST0000006"
Type: Correlation
name: "Aditya_Test_Policy"
description: "Correlate incoming deployment alerts with other alerts."
criteria: "event_provider: OpsCruise AND -status: Closed AND entity_type: deployment"
precedence: 1
category: "alert_handling"
actions:
- type: "correlate"
criteria: "summary: \"Available replicas\""
elementType: "container"
linkType: "child"
query: "event_provider: OpsCruise AND status: Open AND entity_type: container AND related_entities.deployment_name: $alert.entity_name AND related_entities.namespace: $alert.related_entities.namespace"
batchSize: 100
- type: "correlate"
criteria: "summary: \"Available replicas\""
elementType: "pod"
linkType: "child"
query: "event_provider: OpsCruise AND status: Open AND entity_type: pod AND related_entities.deployment_name: $alert.entity_name AND related_entities.namespace: $alert.related_entities.namespace"Type: Enrichment
name: "Enrichment policy"
description: "Enrich OC alerts."
criteria: "event_provider: OpsCruise AND -status: Closed AND related_entities.namespace: \"robot-shop\""
precedence: 1
category: "alert_handling"
actions:
- type: enrich
criteria: "status: Open"
set:
priority: "Low"
description: "QA teamm modified it for testing"